In previous article, I mentioned How To Delete Microsoft Account From Windows 11 but in this aritcle, I have mentioned how we can Check Windows Login History using various possible ways.
You can track unauthorized log-on to your Windows PC by checking its Windows login history. It will help to know when people use the Microsoft account without your consent, and if you need to change your security settings to disallow intruders from accessing your private data.
Read on to learn the different methods for checking your Windows login history.
Ways To Check Windows Login History
There are two quick methods for checking Windows login history on your computer. You can use the computer event viewer or the PowerShell app. Let’s get started with the steps in both methods.
Method 1: Check Windows Login History Using The Event Viewer
Event viewer is a Microsoft Windows NT operating system component that lets administrators and users view event logs on a local or remote computer. these steps to find out how who is currently logged into your computer:
- Click the search icon from the taskbar, type "event viewer" into the text box, and click the Event Viewer app icon on the search results page to open it.
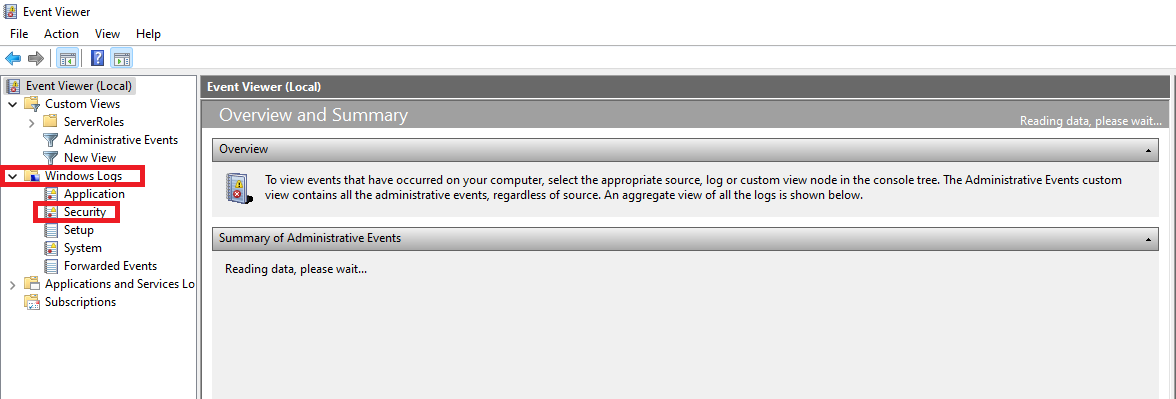
- Navigate to Windows Logs > Security from the left pane of the event viewer window, then click on Security.
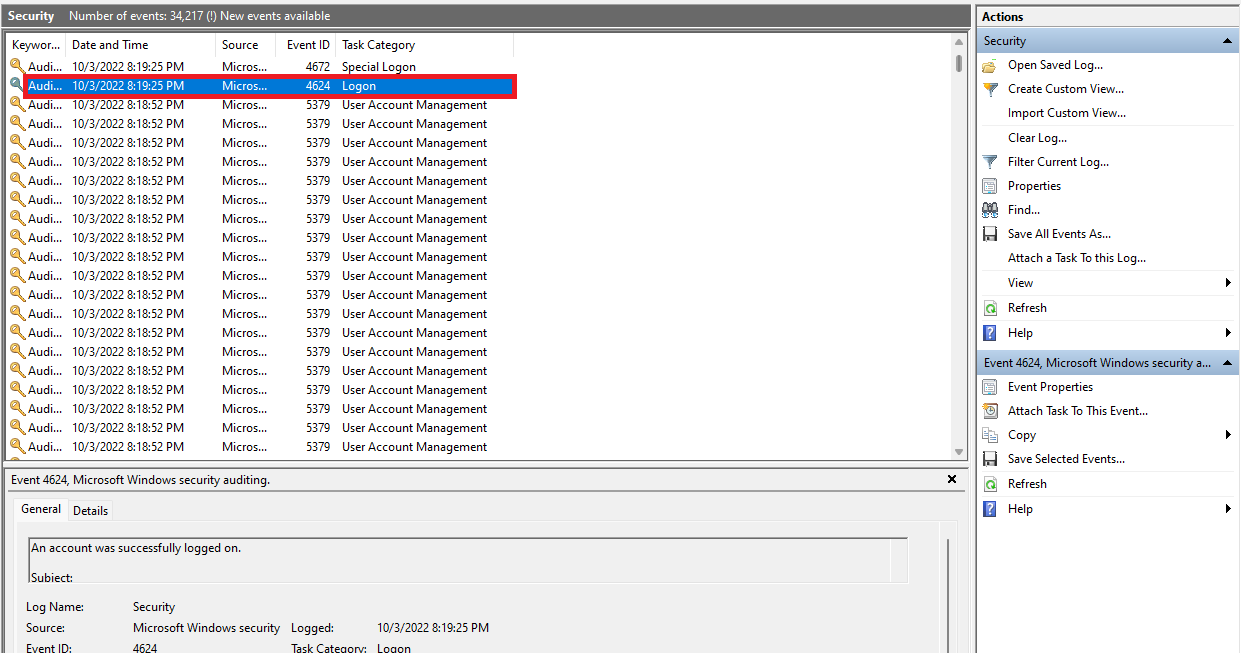
- Scroll through the events under the security section in the middle pane to locate the event with the 4624 event ID and open it to see the details of the account that has logged on to your account.
- Check the General section to see the Account Name; it is the account that has logged on to your computer, and you will also see the logged time on the window.
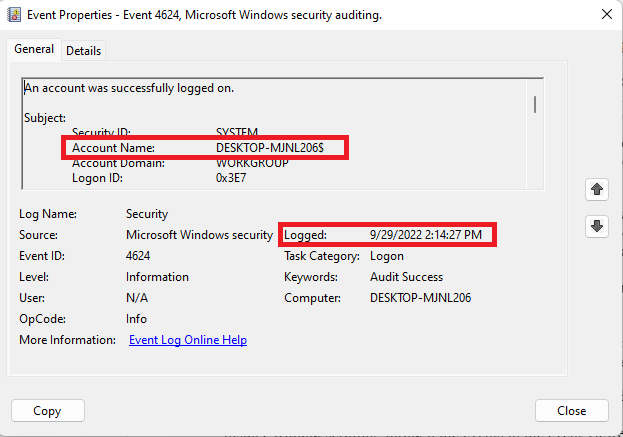
The logged time is when an account accessed your device, but the record you just viewed is one of the several log-in records on your computer.
Now, the biggest question now is, how do you check all the Windows logon history without scrolling through the events in the event viewer or selecting each event with 4624 ID successively?
The best way out is to create a custom view; It lets you filter the events you want to see by checking the Windows login history over a period. To do this:
- Click on Create Custom View under the security section in the action pane.
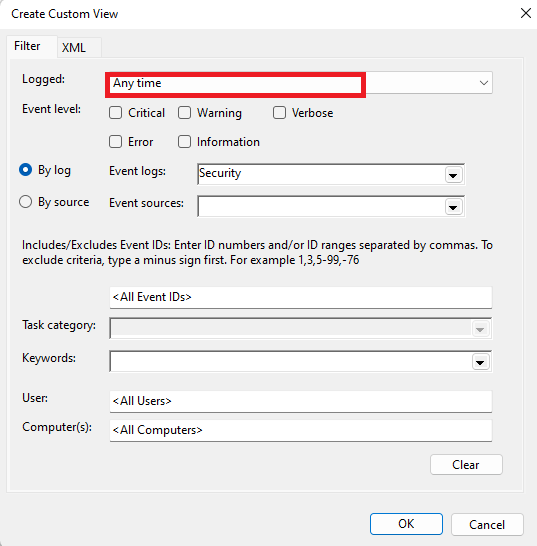
- Choose a time range for Logged; you will only see the login history over the period you select here.
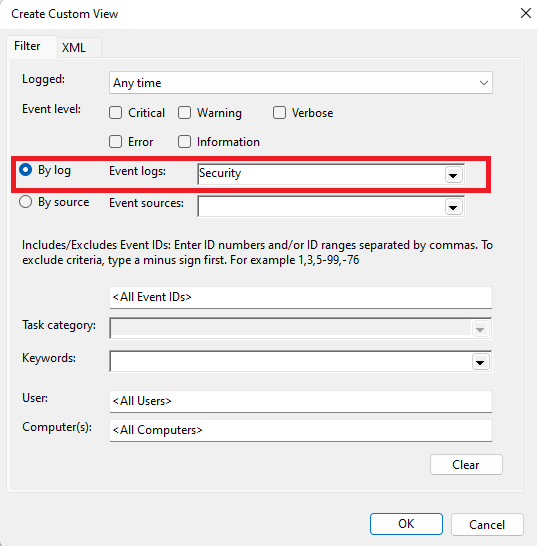
- Ensure the radio button beside the By log option is active and the Security option is in the Event logs tab; do not change these two.
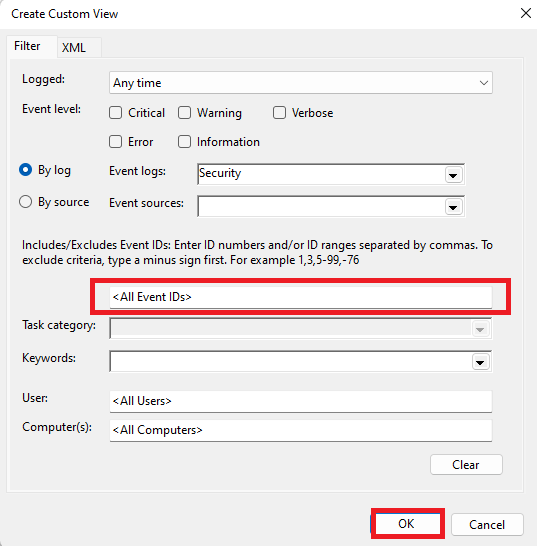
- Type 4624 in the All Event IDs box, then Click OK.
- Save the filter to a custom view by entering a name and clicking OK.
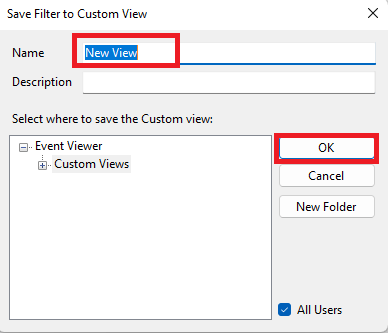
The system will display only the Windows login history within the selected period, and you can check them more easily.
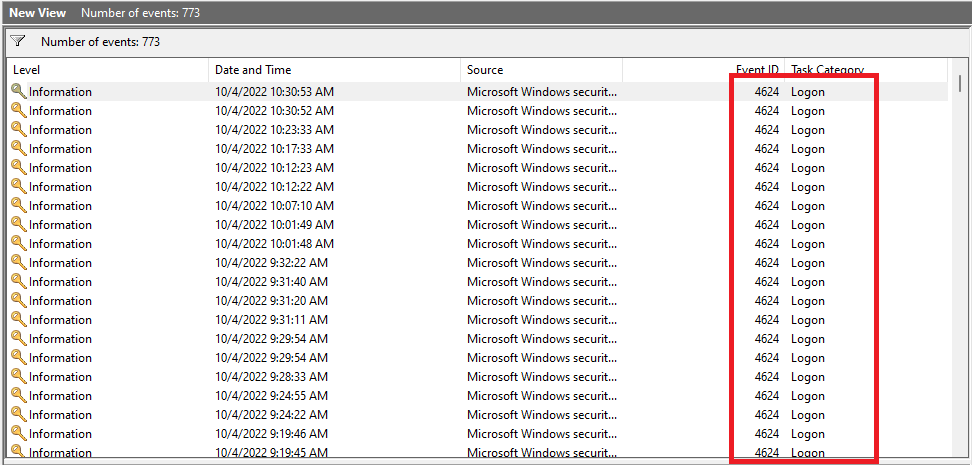
Method 2: How To Check Windows Login History Using PowerShell
Another effective way to check Windows login history is to use the PowerShell application. Below are the steps to do this:
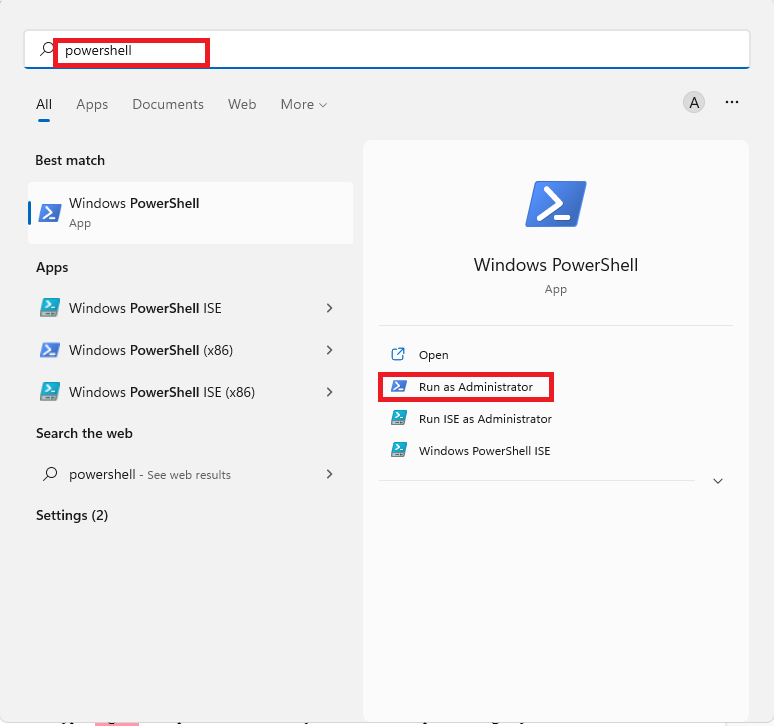
- Press Windows + S to open the Windows search option, type PowerShell in the field, and select Run as administrator to run PowerShell with admin privileges.
- Next, paste the command below into PowerShell.
Get-EventLog security | Where-Object {$_.TimeGenerated -gt '2/10/20'} | Where-Object {($_.InstanceID -eq 4634) -or ($_.InstanceID -eq 4624)} | Select-Object Index,TimeGenerated,InstanceID, Message
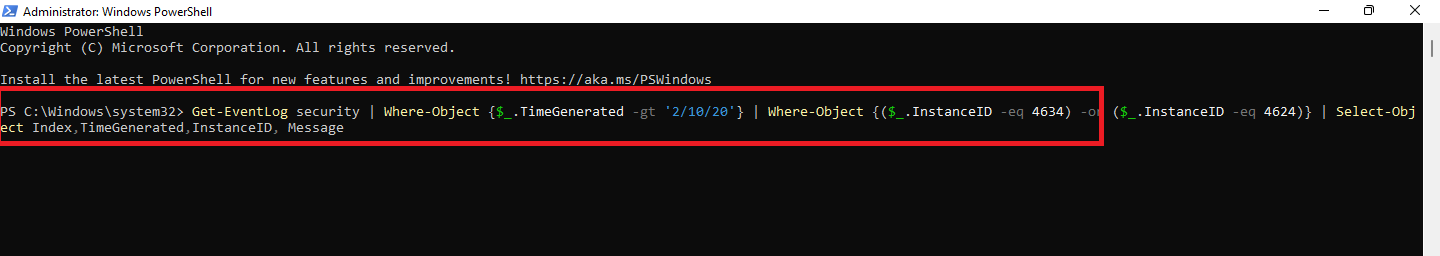
In this code,
- Get-EventLog lets you access the Event Log on local or remote computers.
- The first Where-Object uses the variable $.EventID to compare the Event ID property with the specified value. The date is specified here.
- The first Where-Object specifies the two Event IDs you want. Here, the value is 4624 (EventId for login).
- Select-Object lets you return only the output columns you need to have.
How To Check Windows Login History If All Logs Have Been cleared
A third party that logs in to your computer may clear the Windows login history to hide their login record; However, you can still check the Windows login history in the Windows Registry Editor as follows:
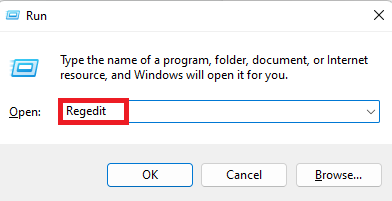
- Press Windows + R simultaneously to open the Run command window.
- Type Regedit, press the Enter key, then click Yes in the User Account Control prompt to open the Registry Editor.
- Paste the path below in the Registry Editor address bar at the top of the window, or you can follow the path successively.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System

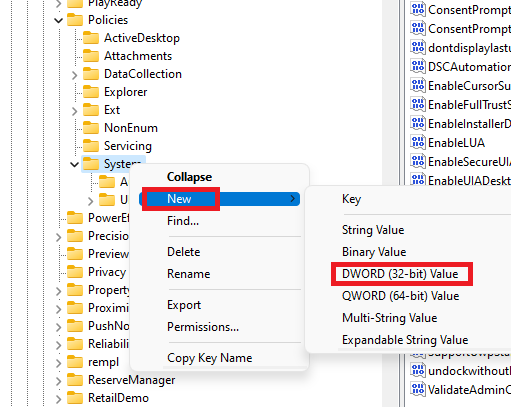
- Right-click on System and navigate to New > DWORD (32-bit) Value.
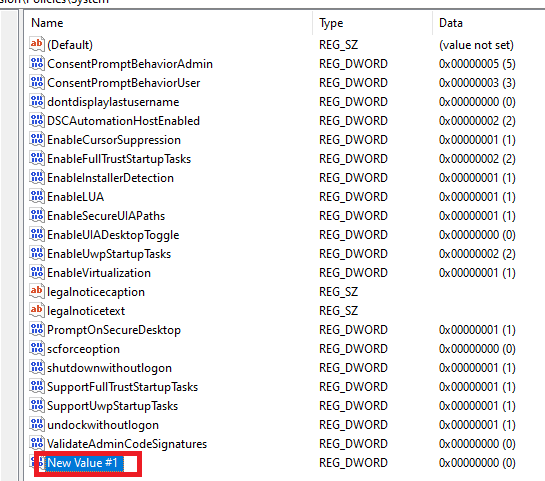
- You will see a new value created on the right pane.
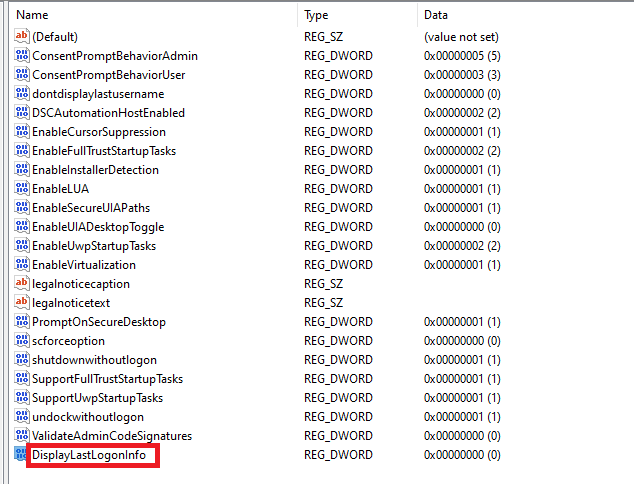
- Rename the new value as "DisplayLastLogonInfo".
- Double-click DisplayLastLogonInfo and set the value data to 1, then click OK.
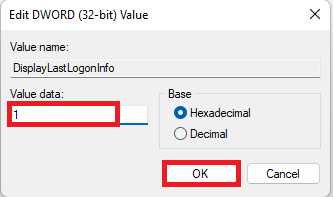
- Close the Registry Editor.
- Restart your computer to effect the change, and it will display recent successful and unsuccessful login attempts when you sign in.
To disable this feature, you can delete the DisplayLastLogonInfo DWORD value you created or set its value data to 0 in the Registry Editor.
Conclusion
Use any of the three options above to check Windows login history on your computer, and you will know when someone accesses your computer without your consent.
You may also like to read:
How To Use Fraction (Not "/") In Google Docs
What Is Replika AI? How Safe Is Replika AI?
How To Change Drive Icon In Windows 10/11
Best Free Z-Library Alternatives (Open Source)
How to change gmail background
Steps to export google calendar to google sheets
How to Set Bing Wallpaper as Windows Desktop Background Daily